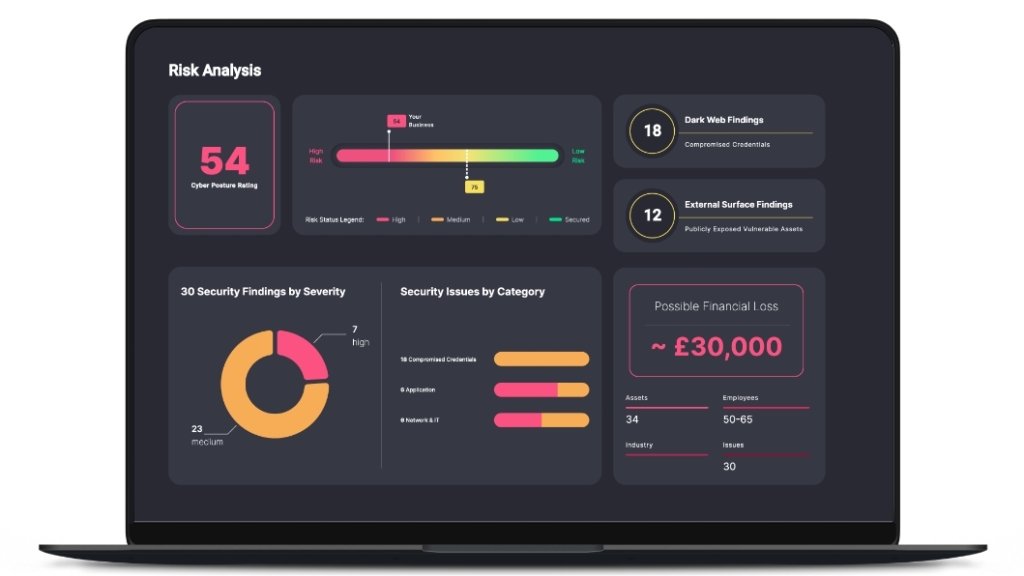
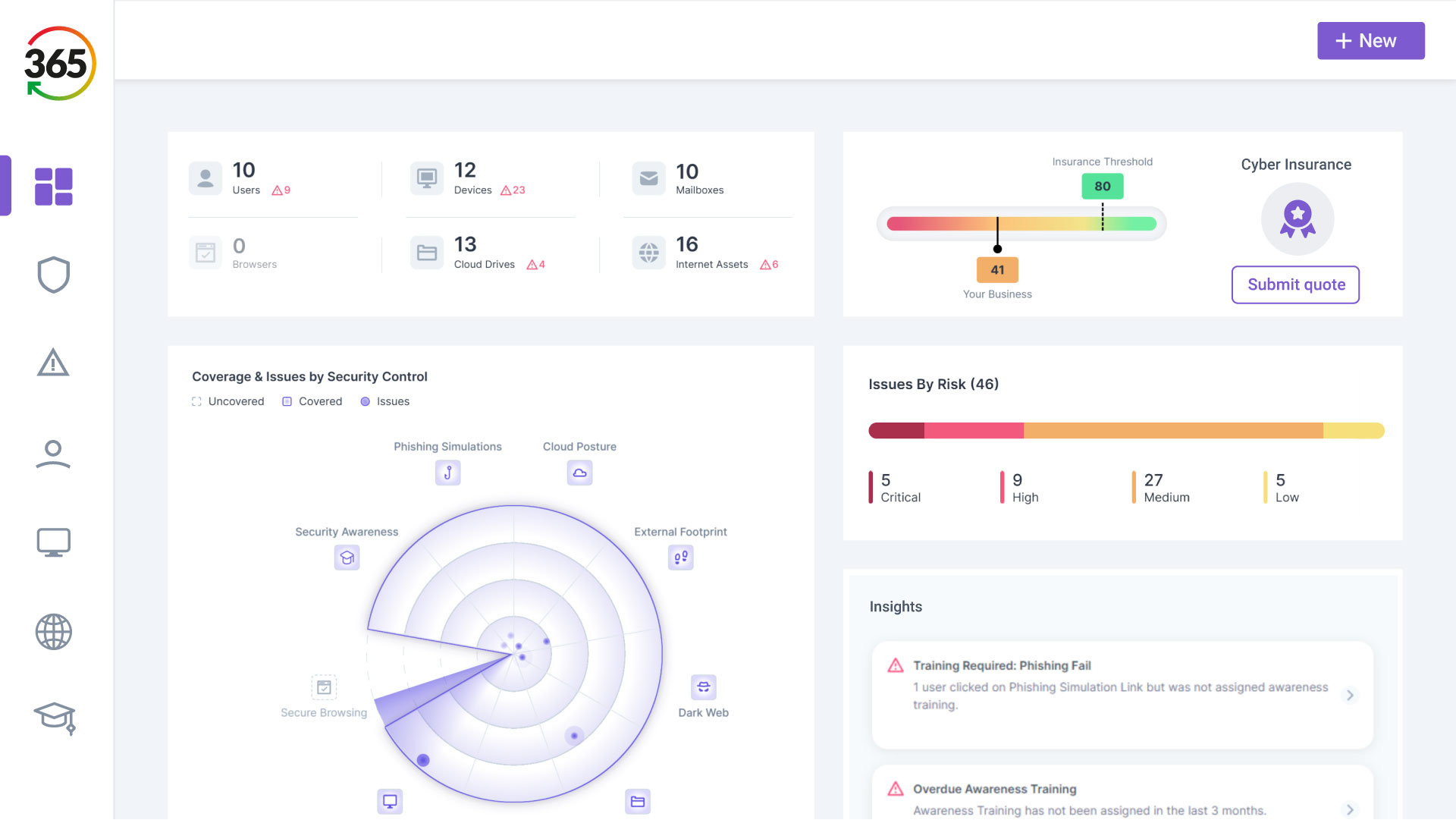
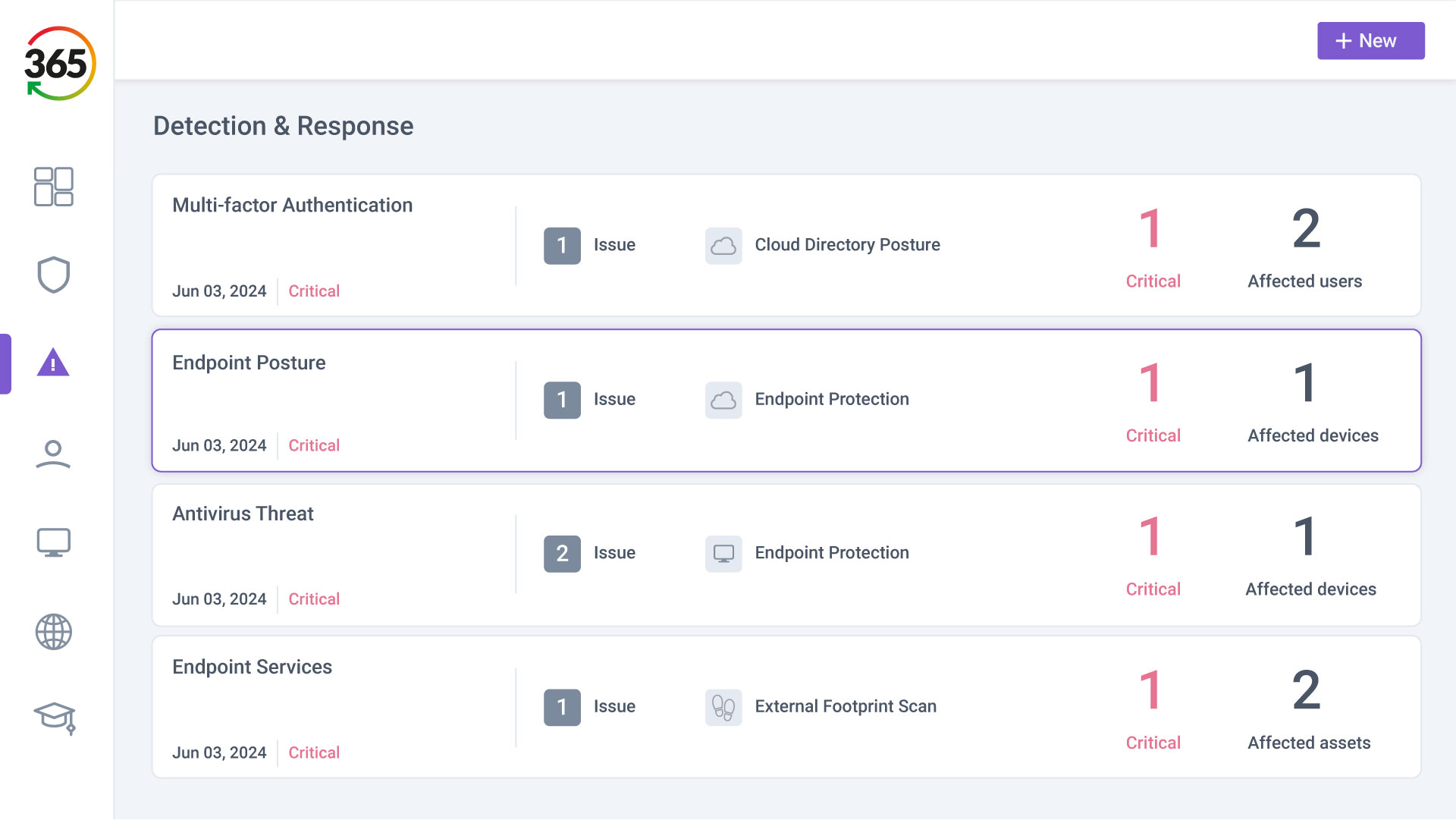
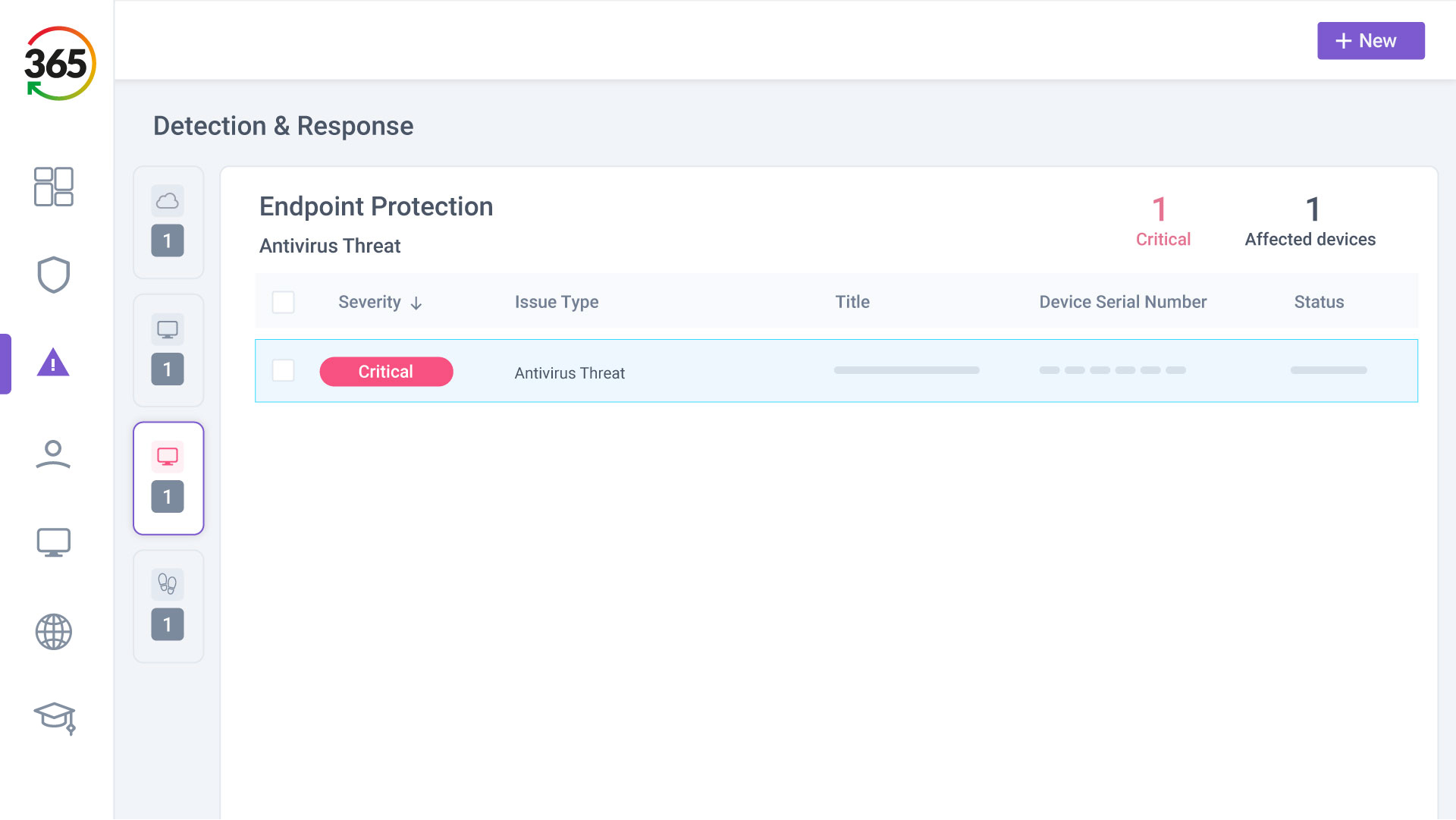
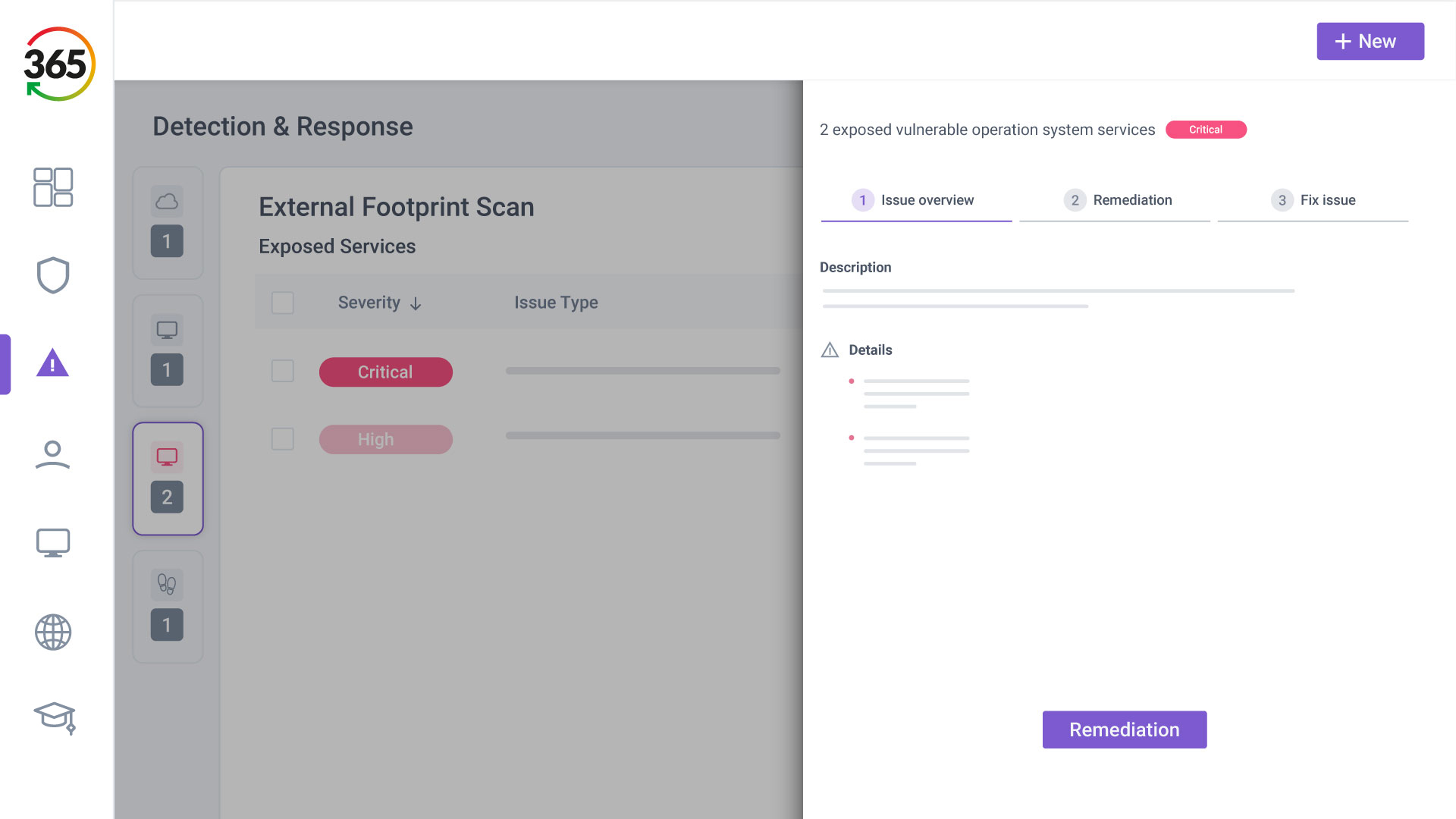
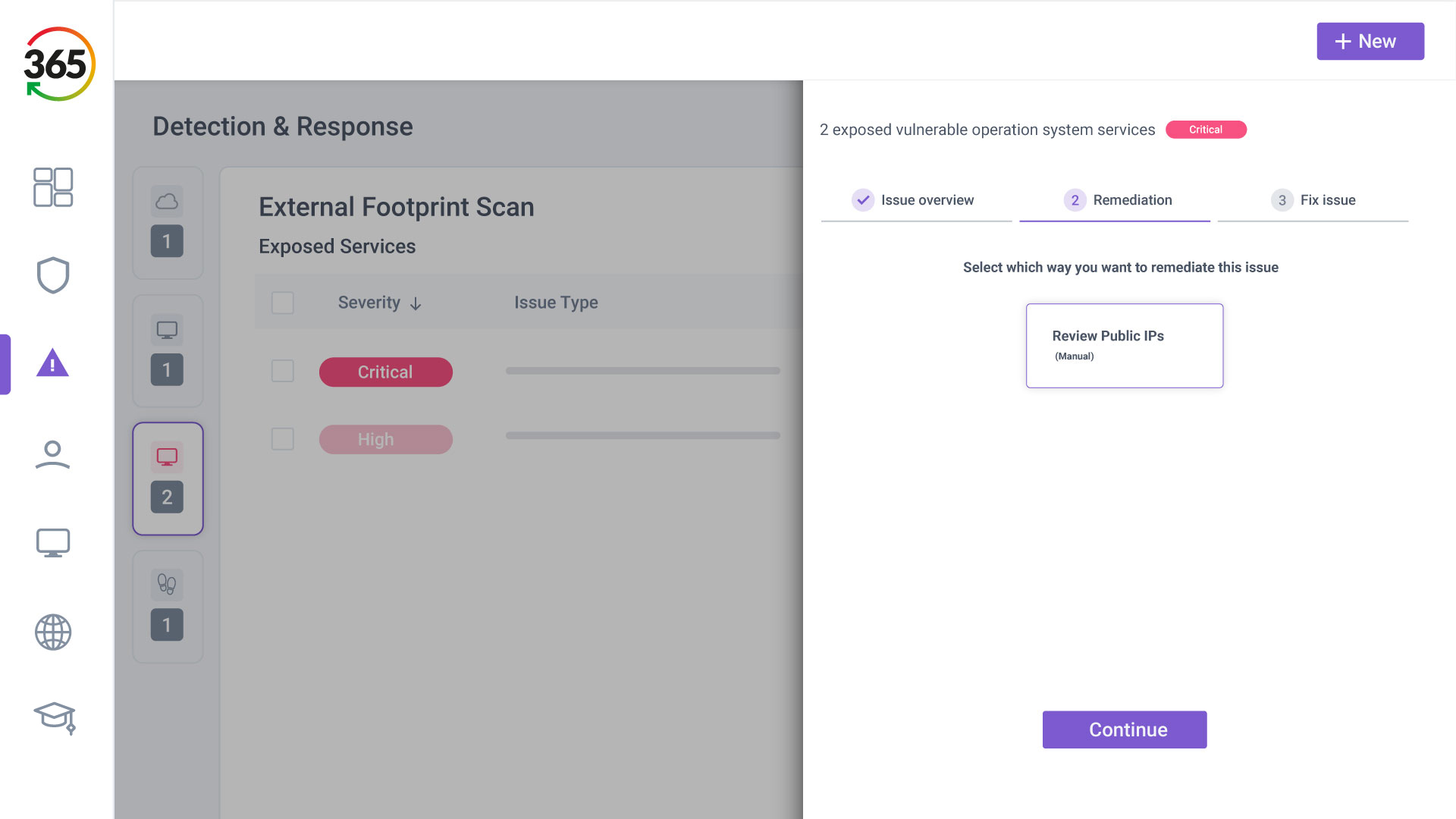
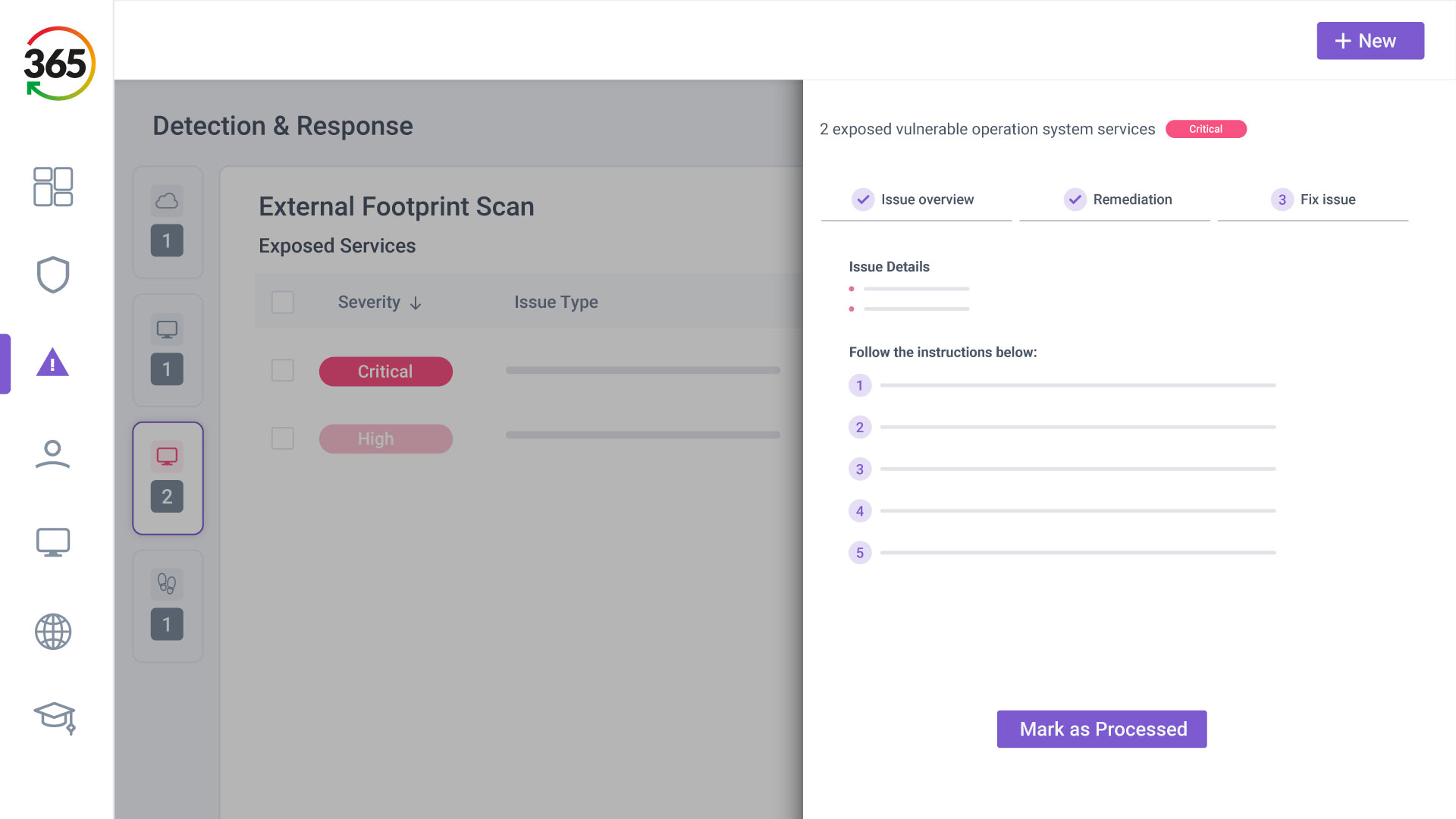
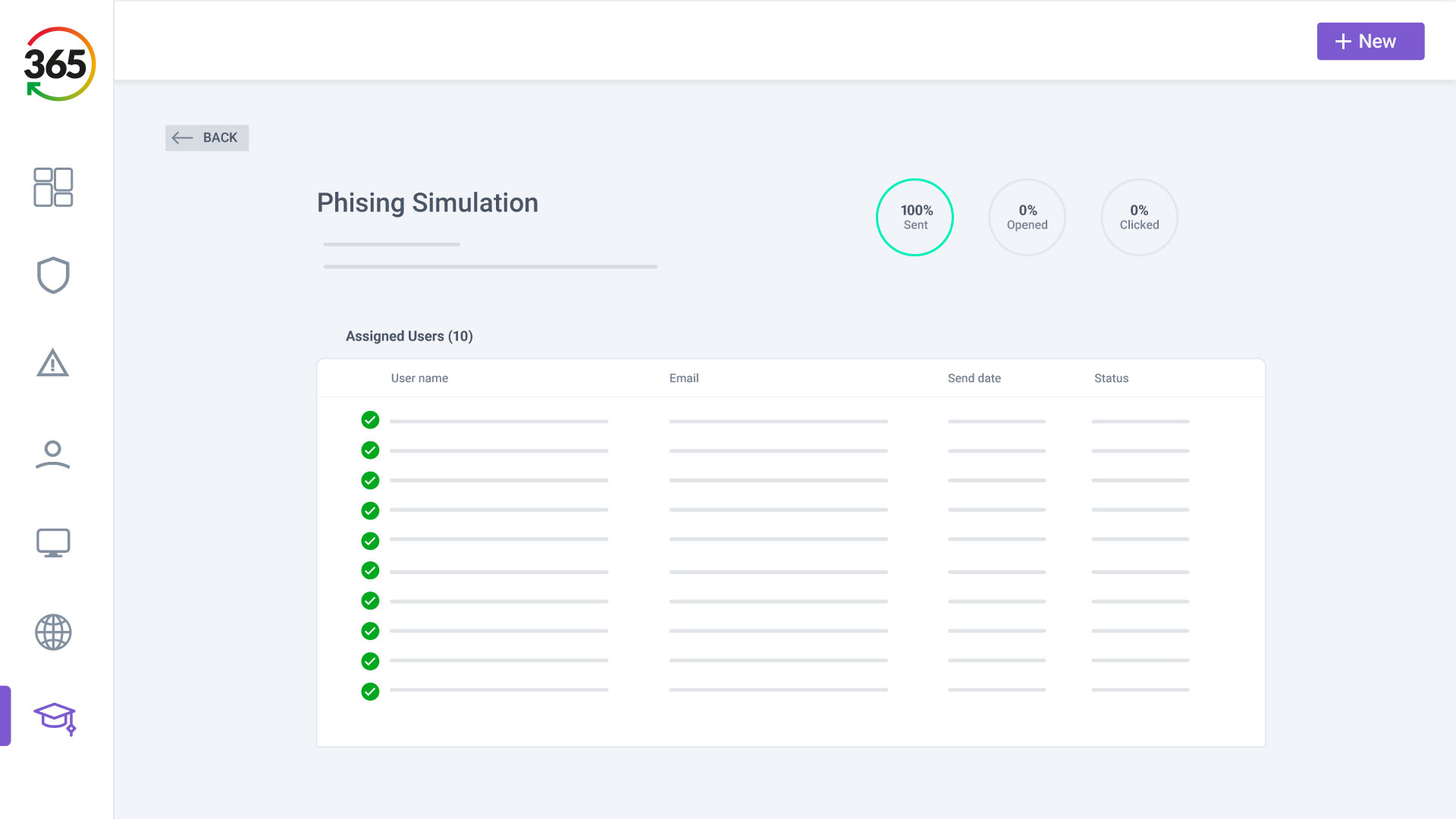
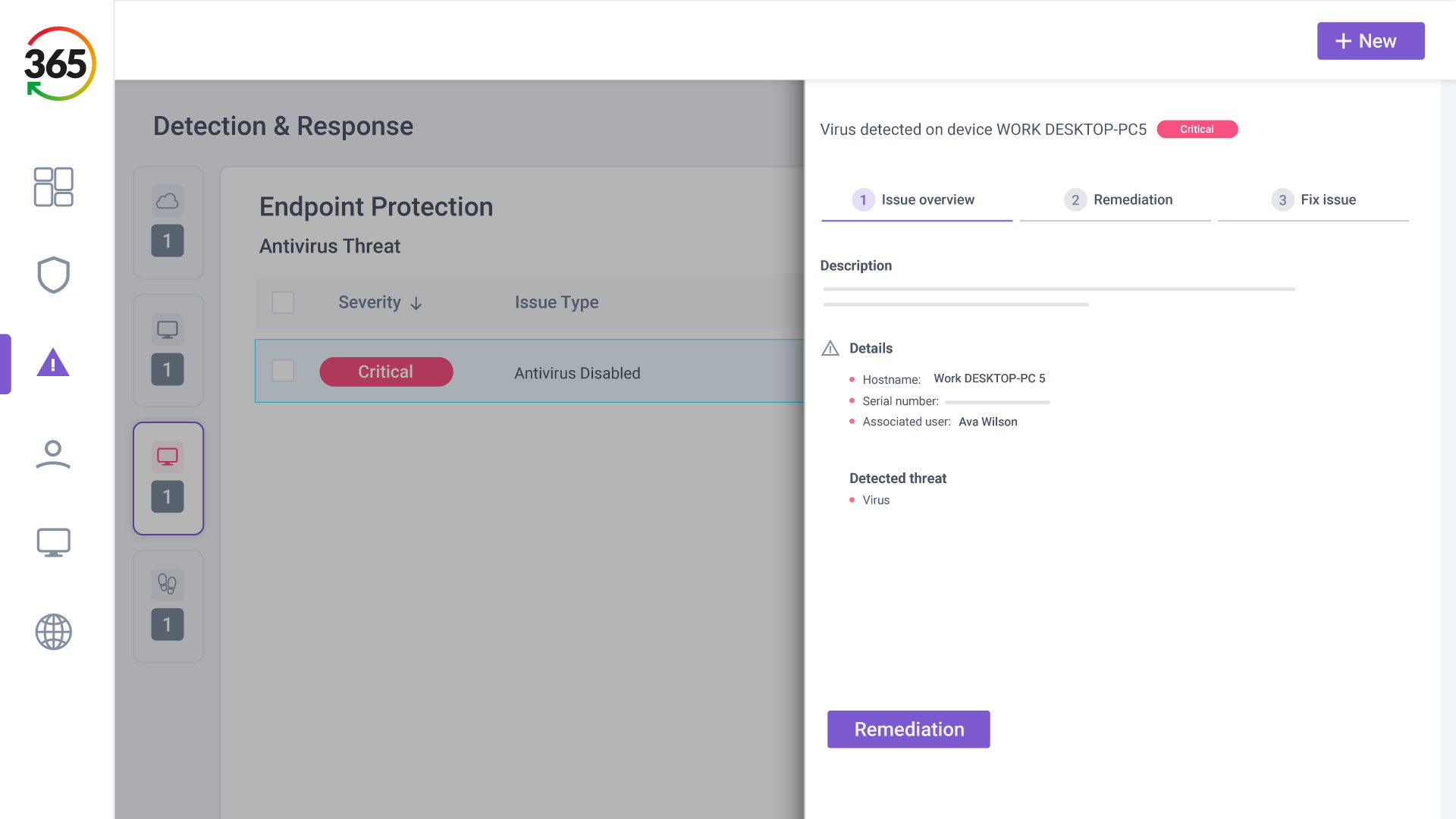
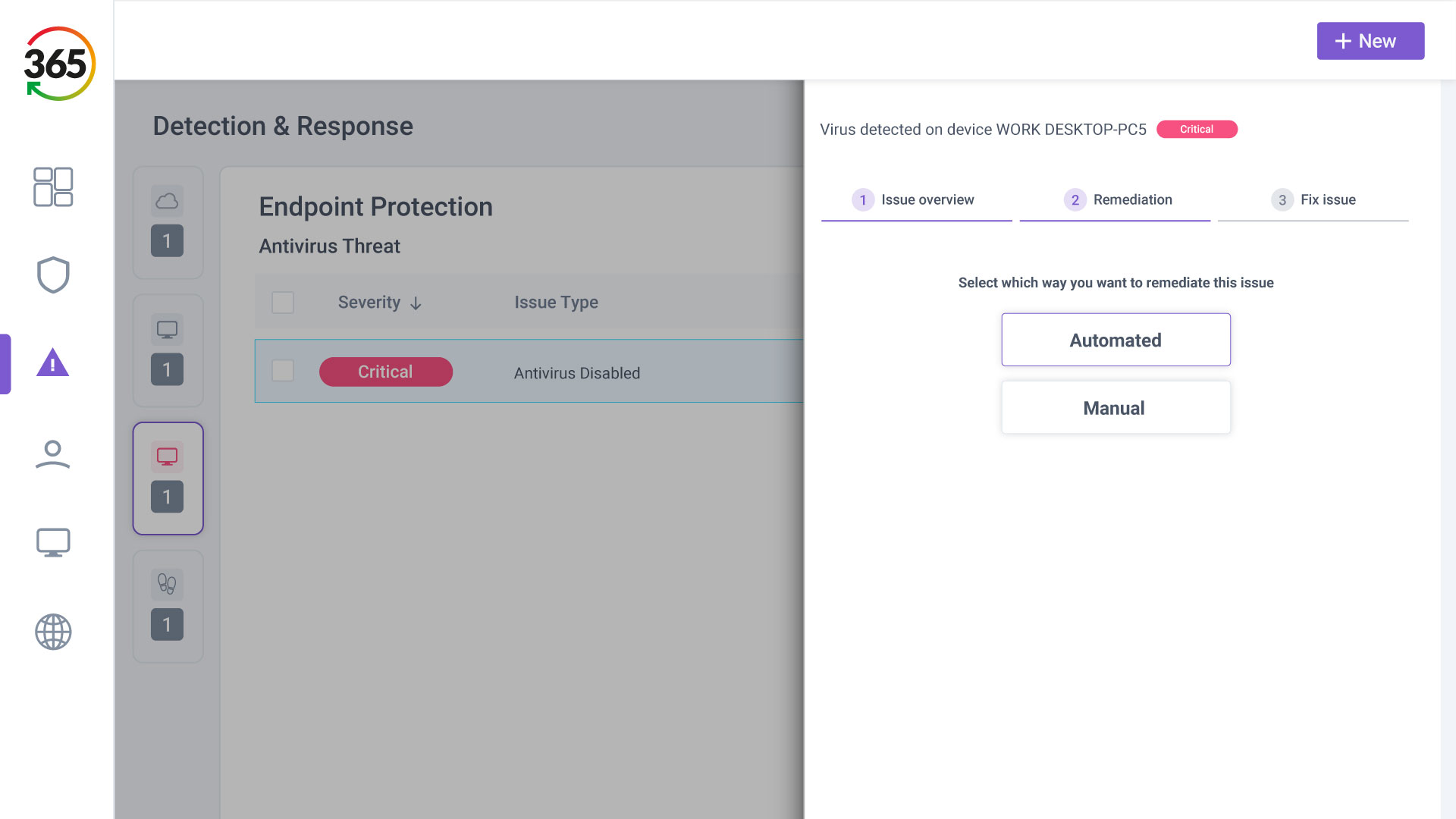
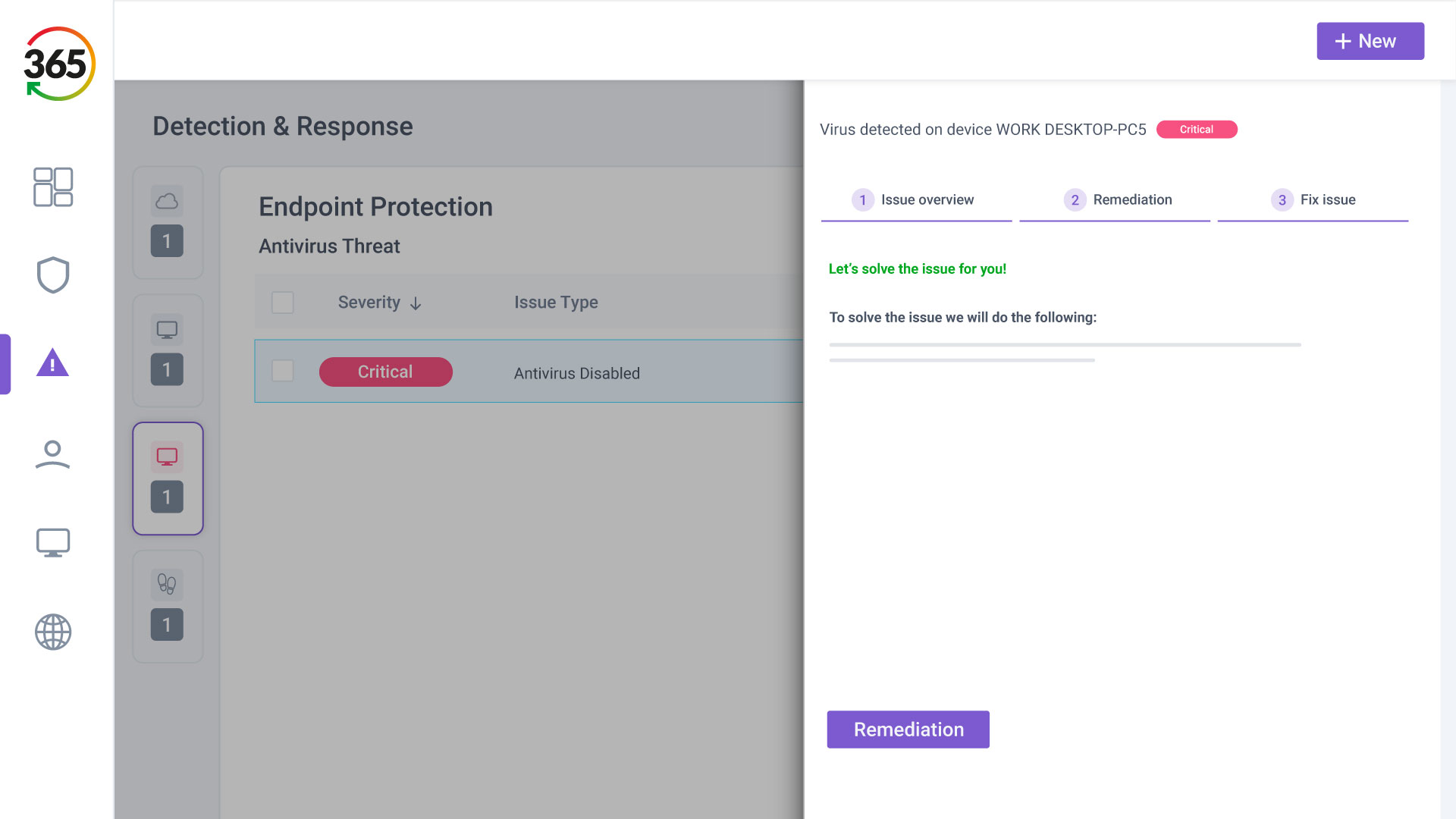
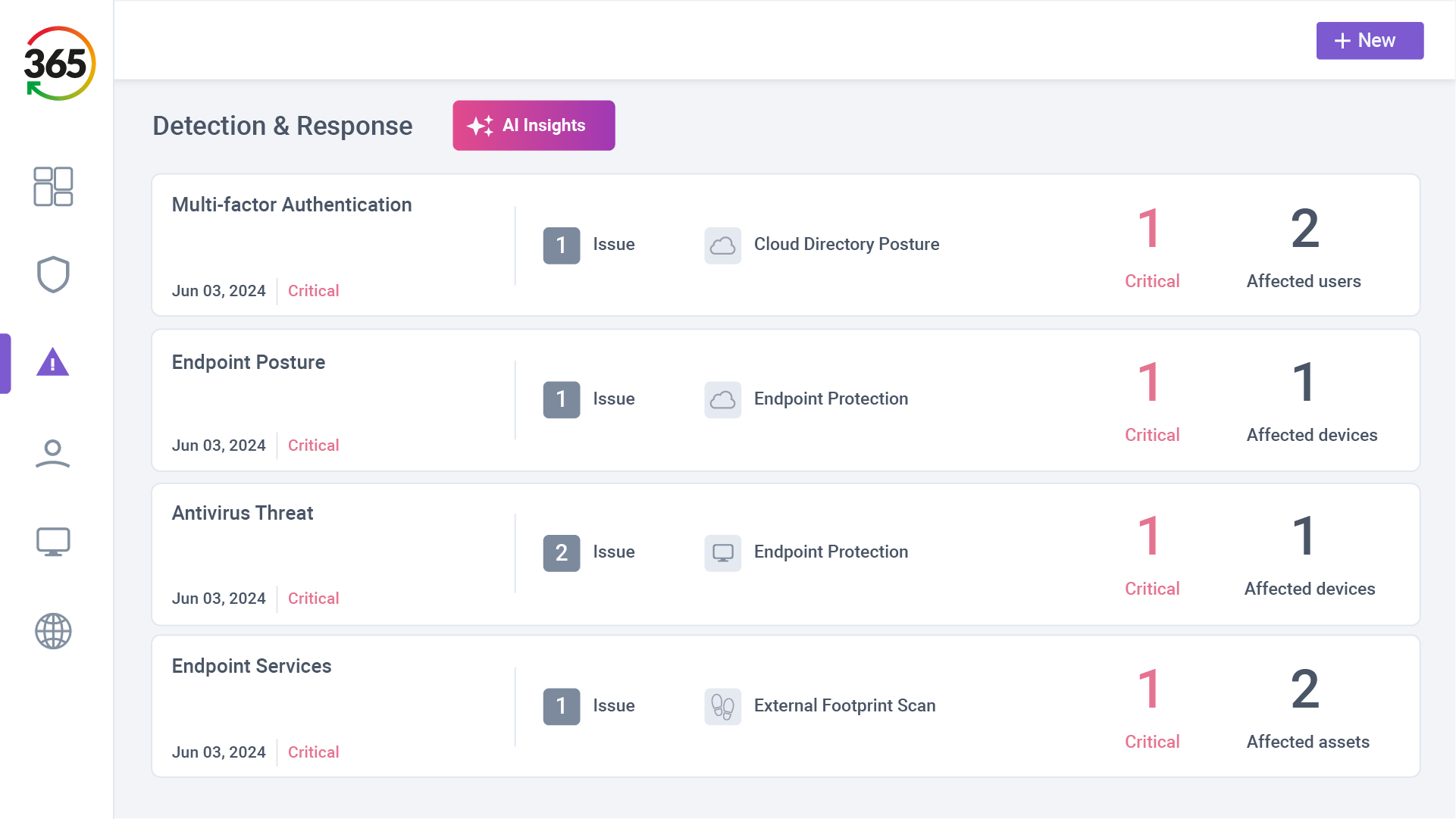
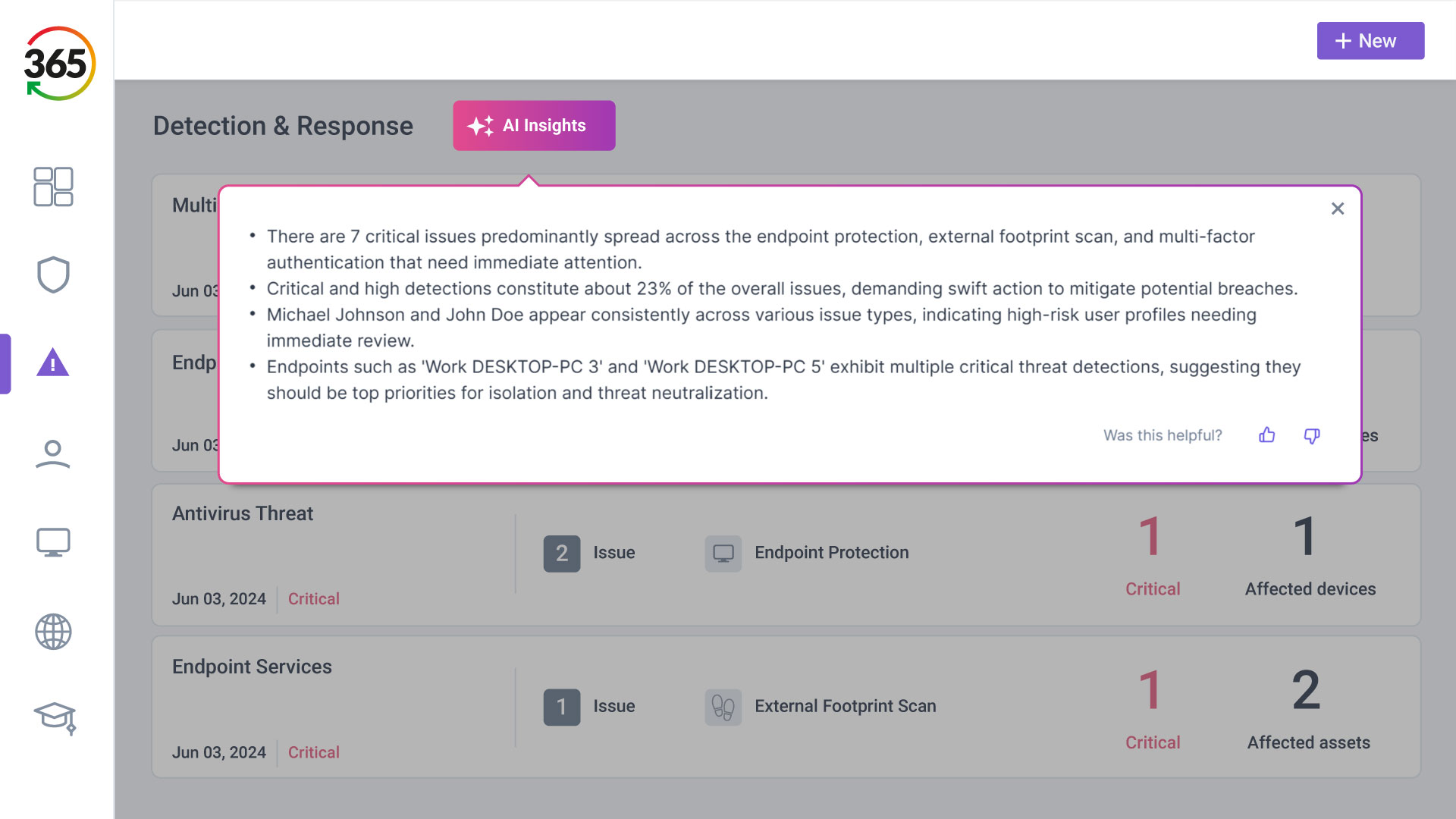
FIND, FIX, SECURE and INSURE
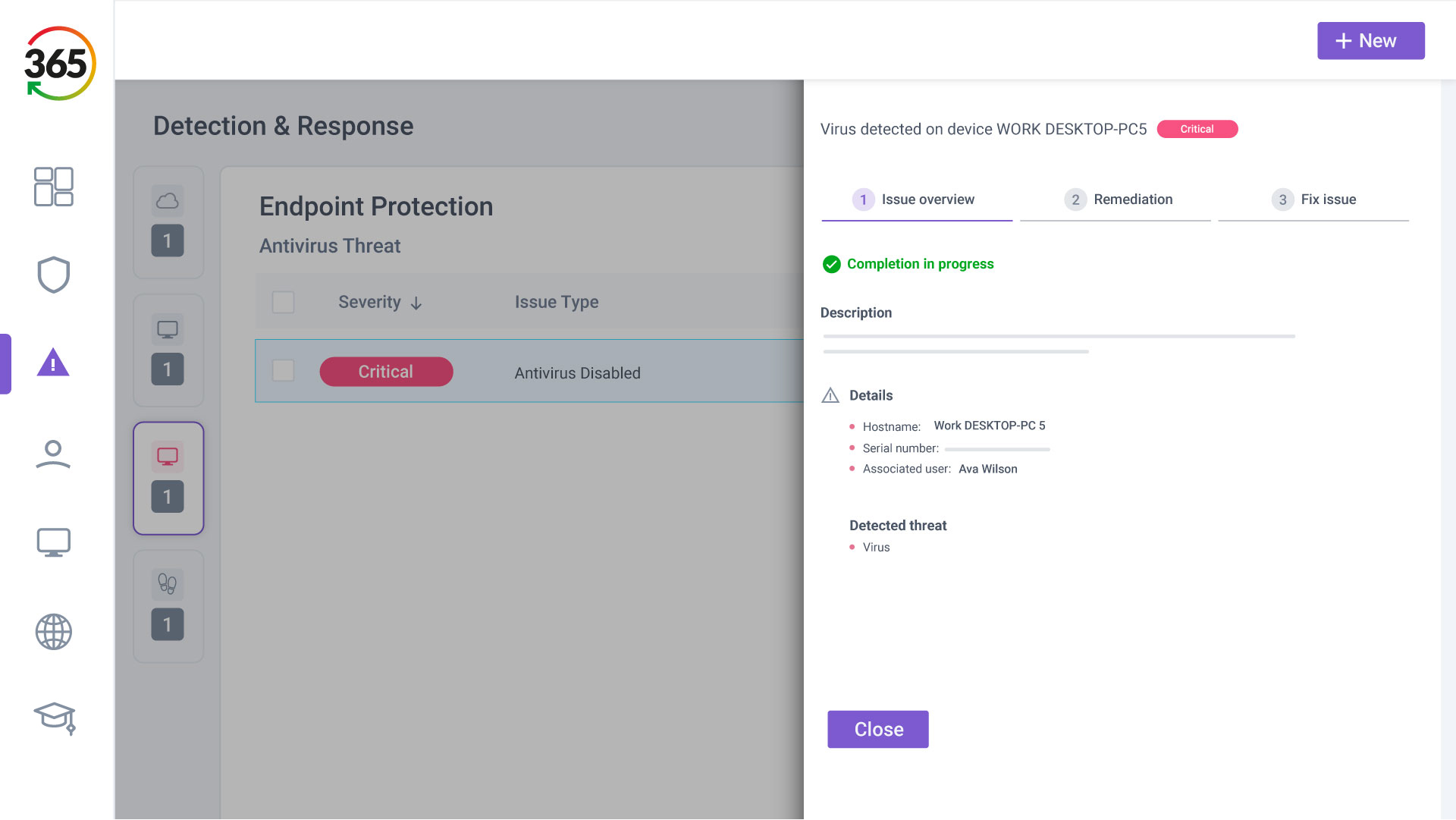
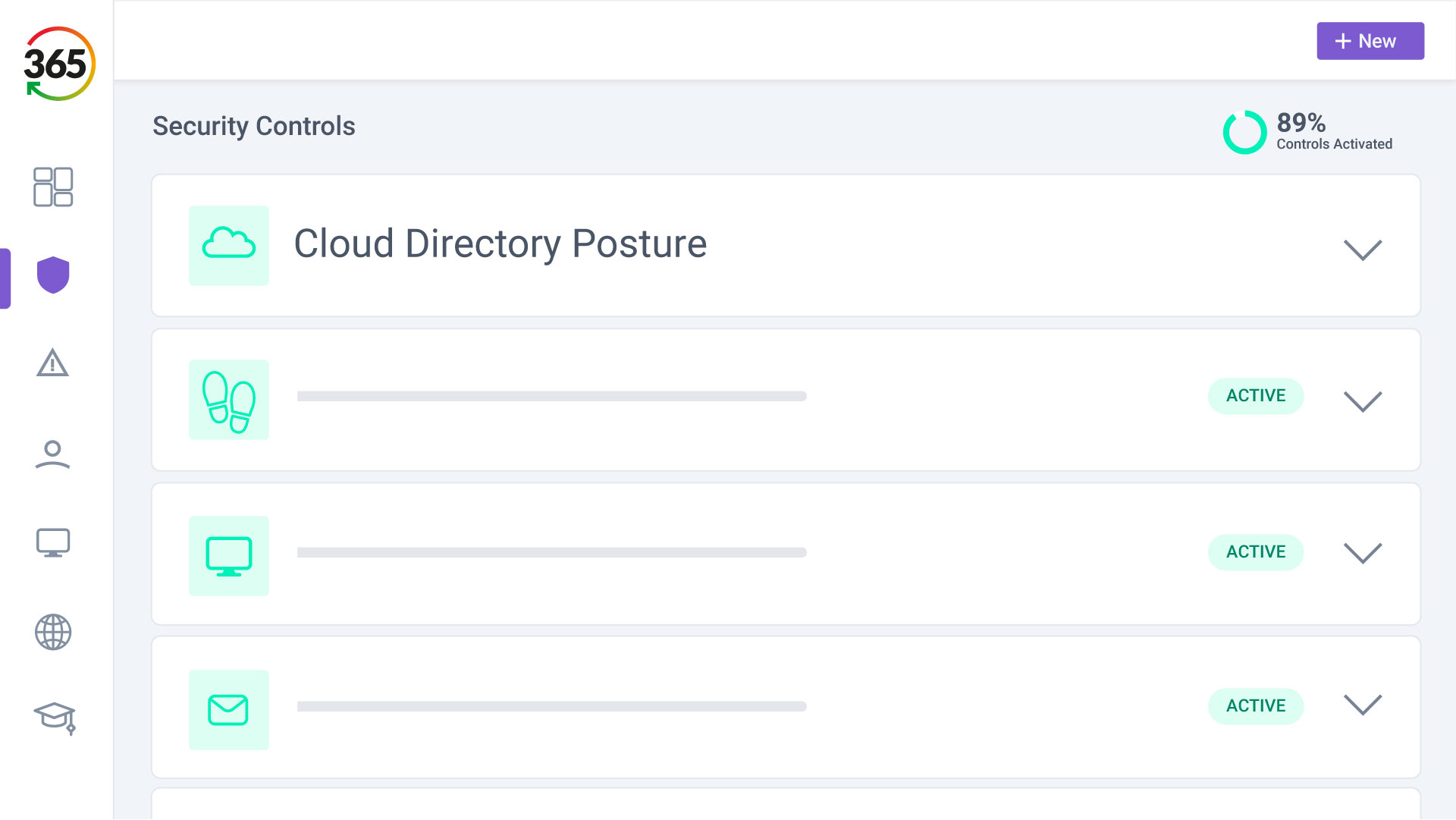
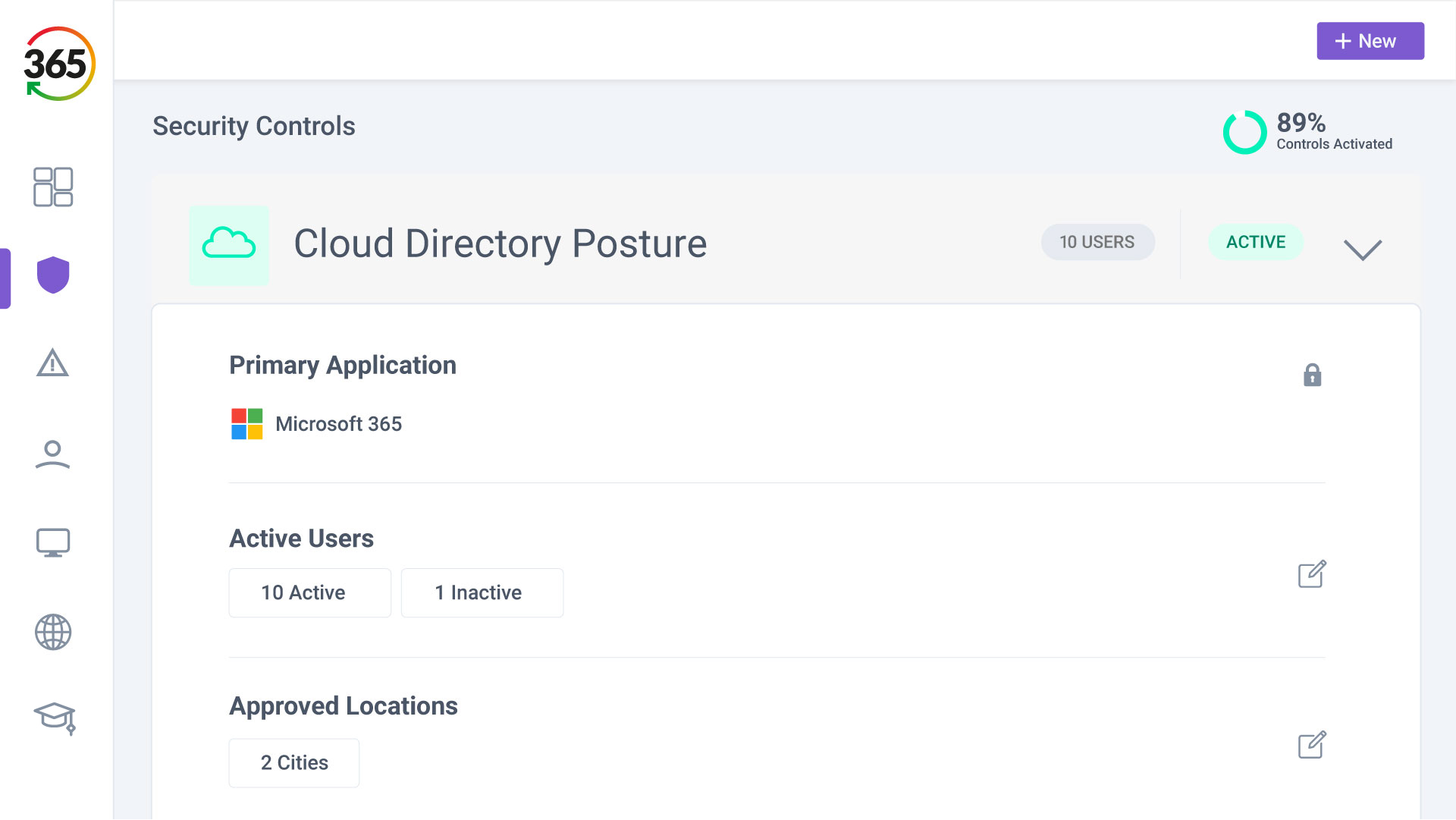
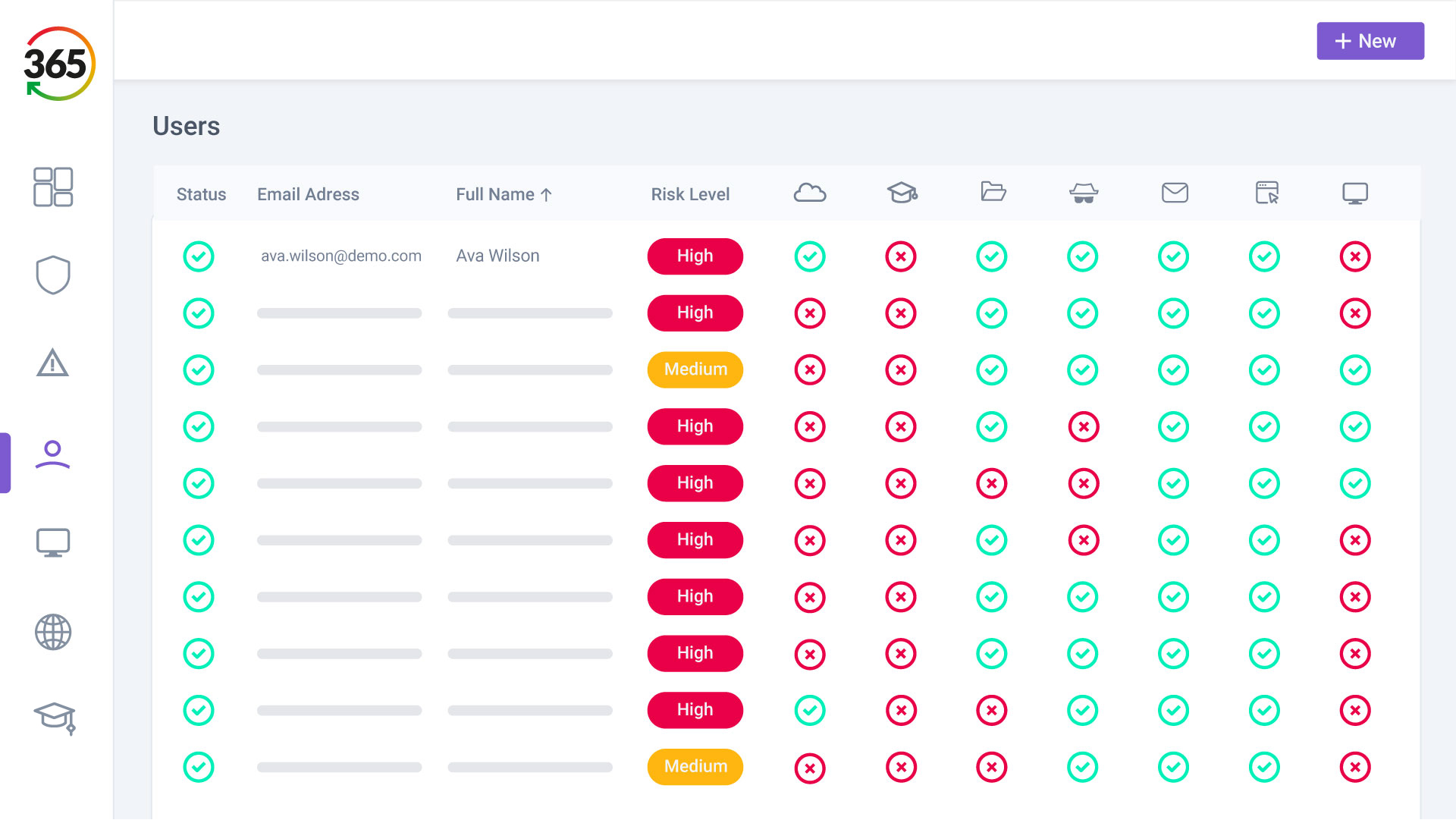
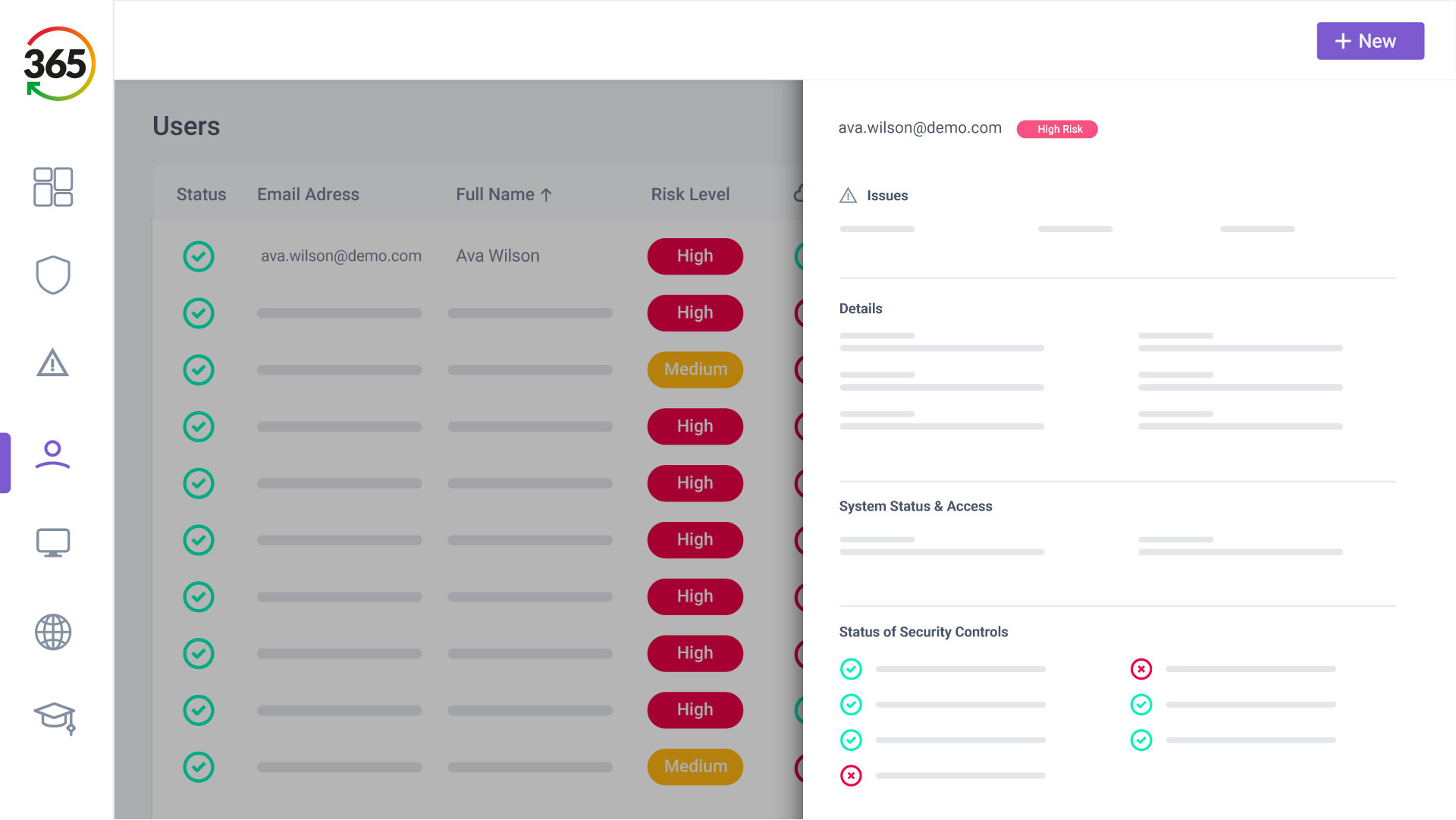
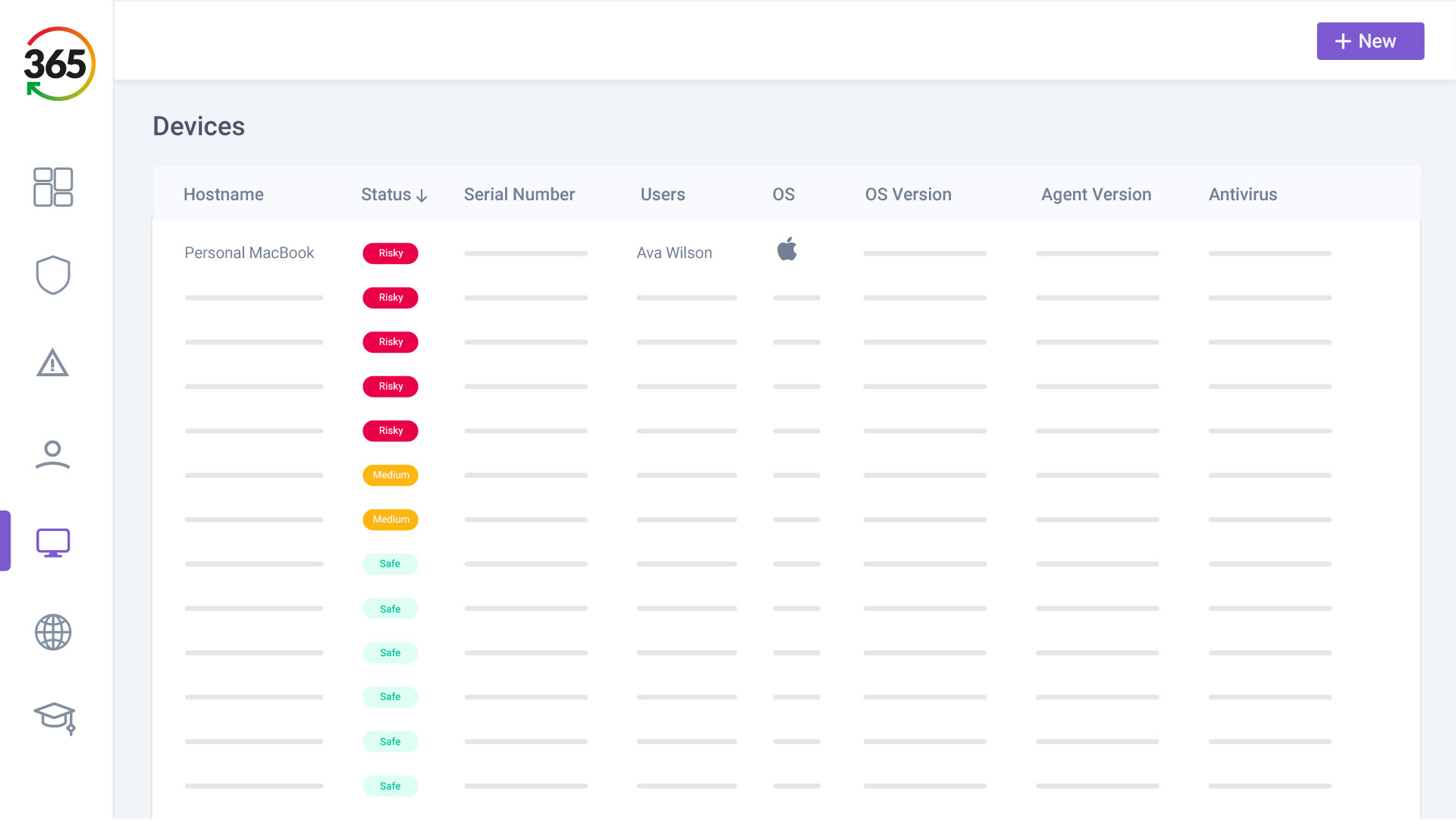
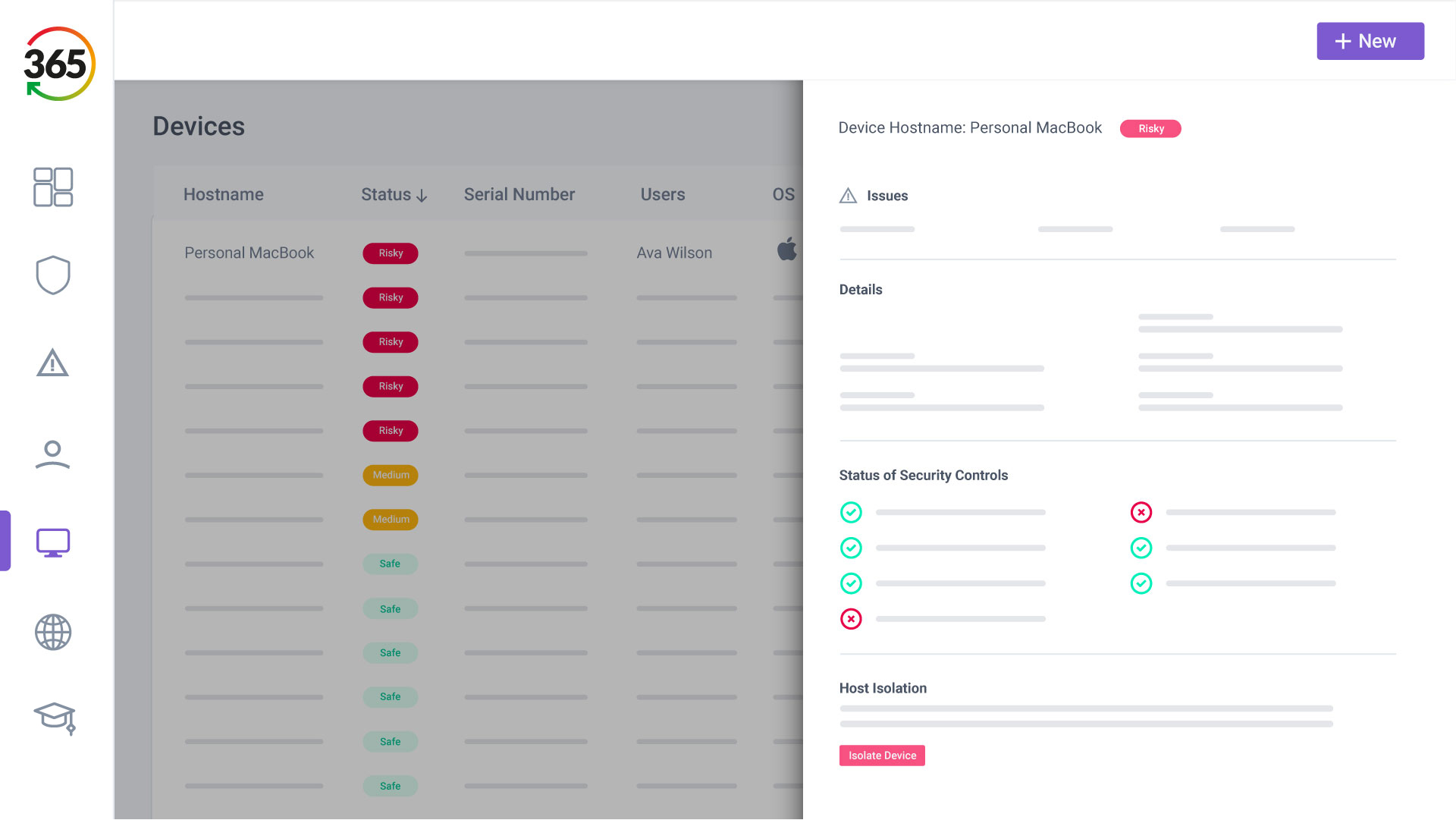
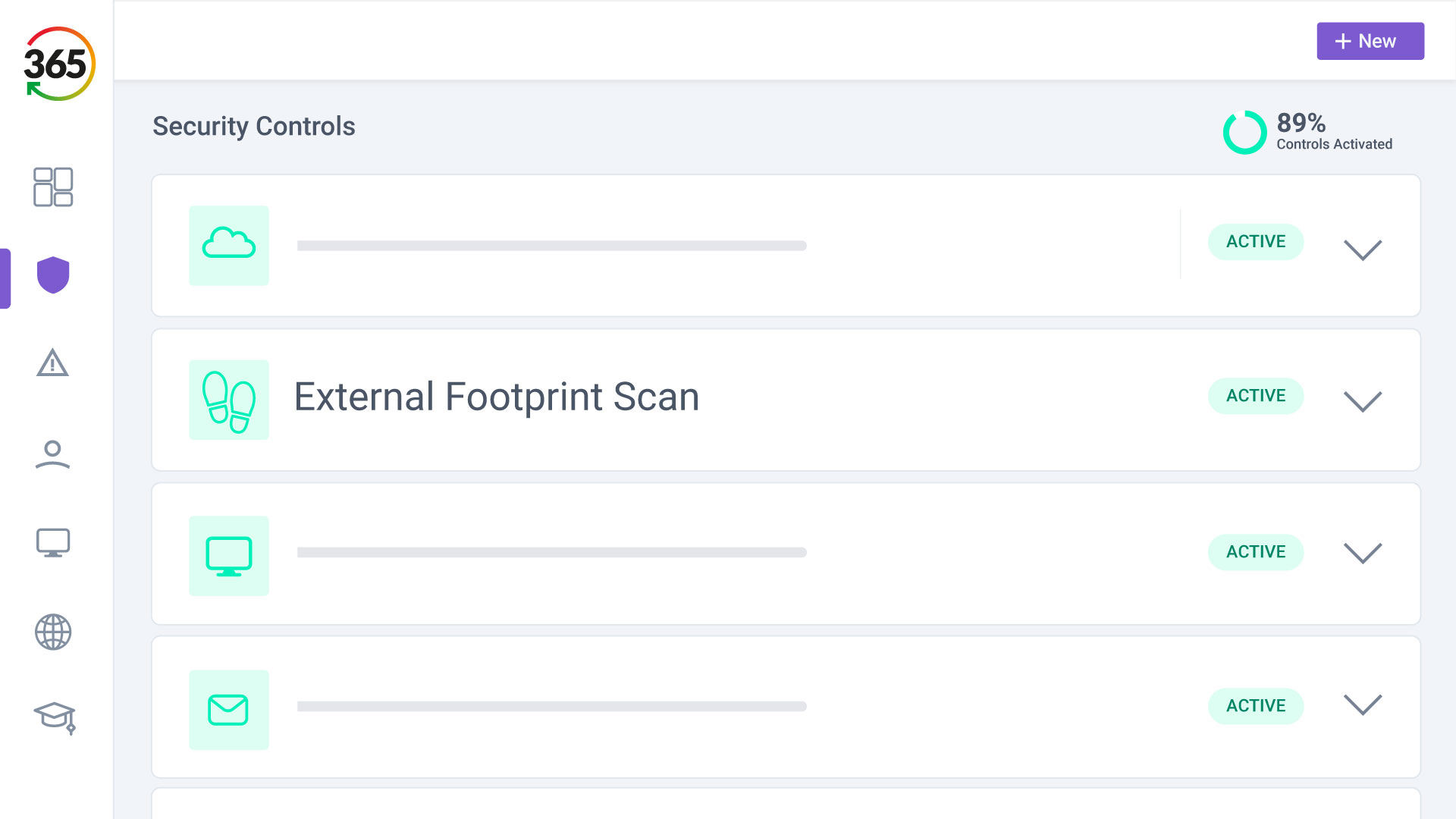
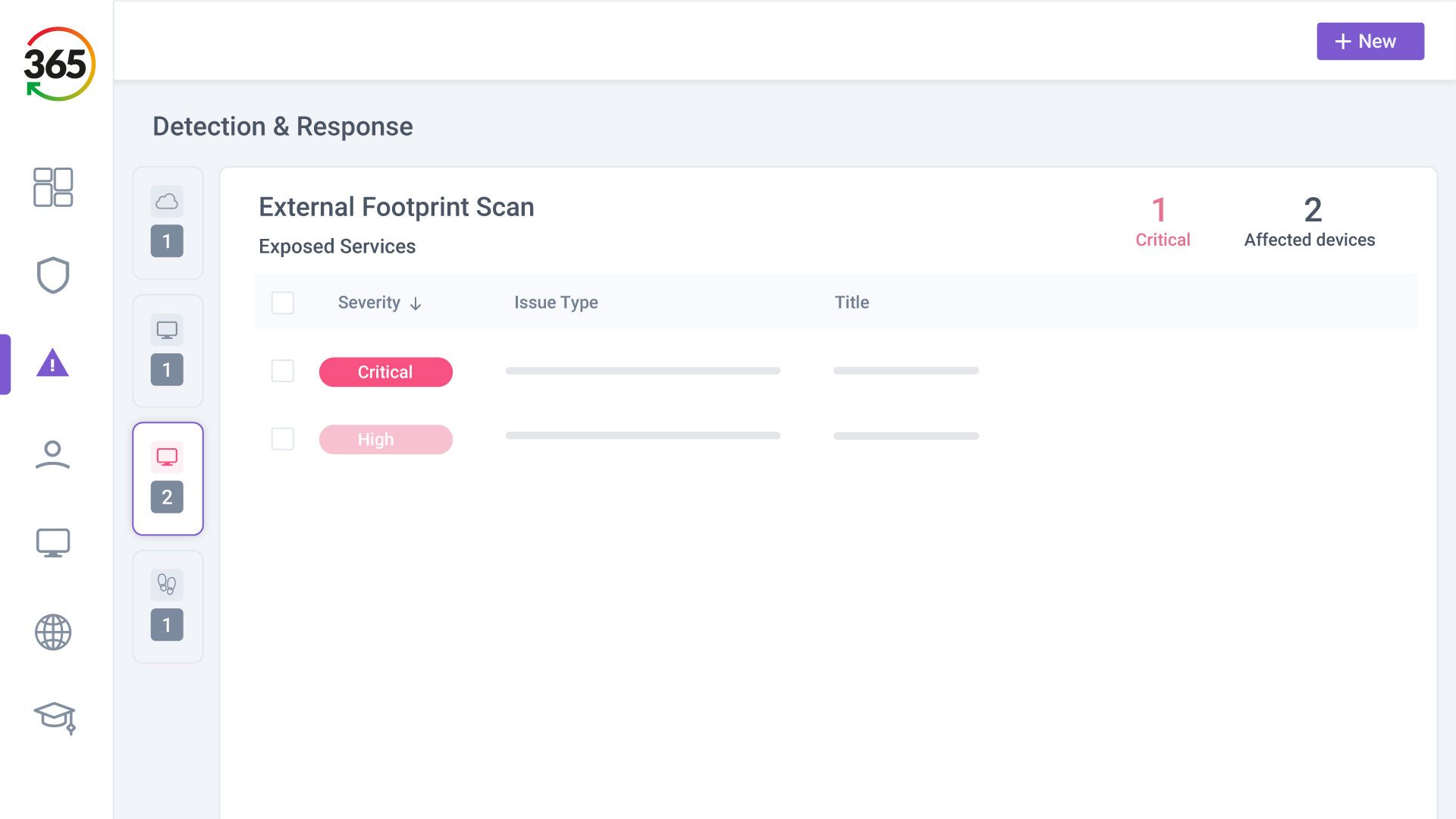
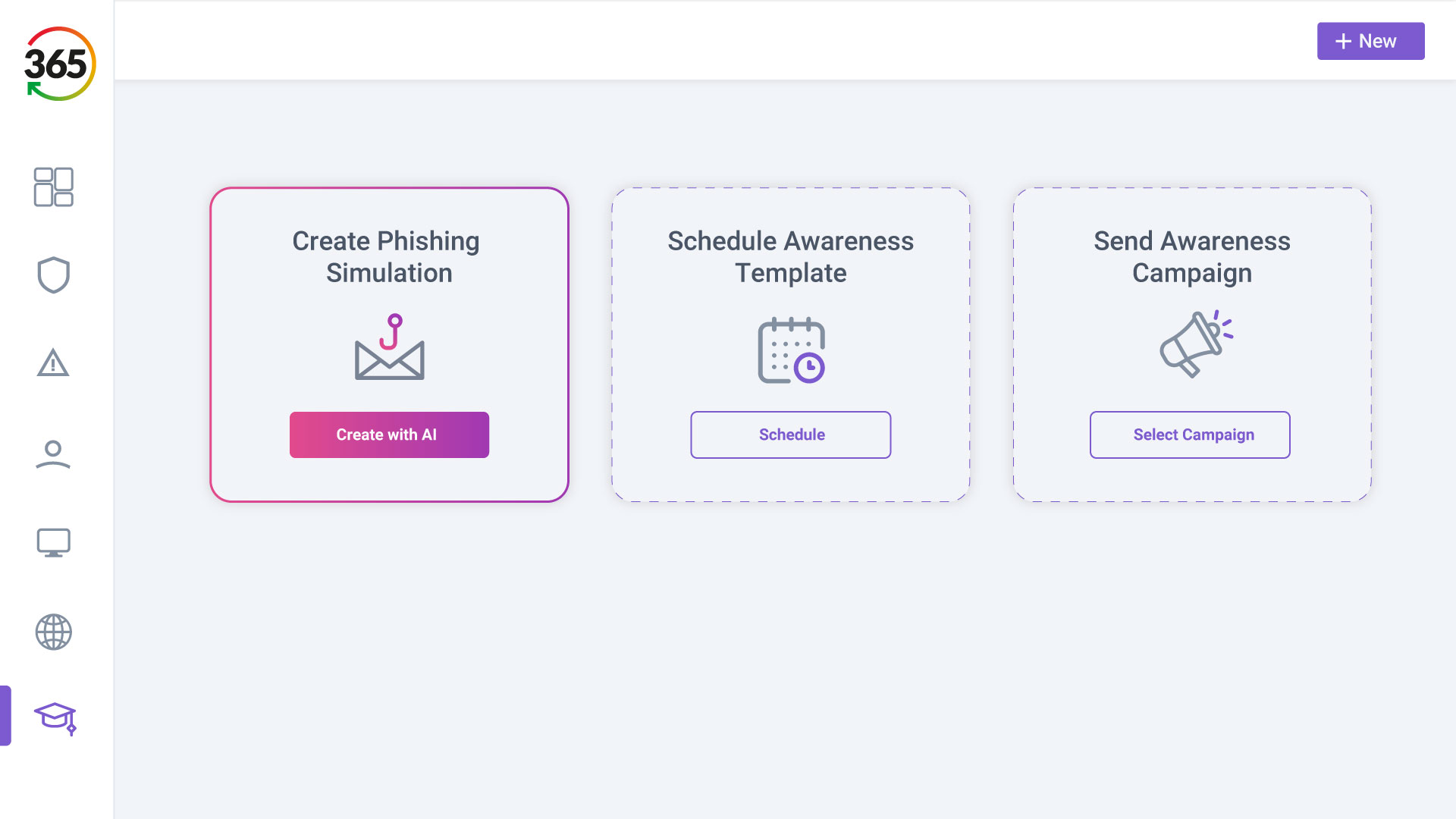
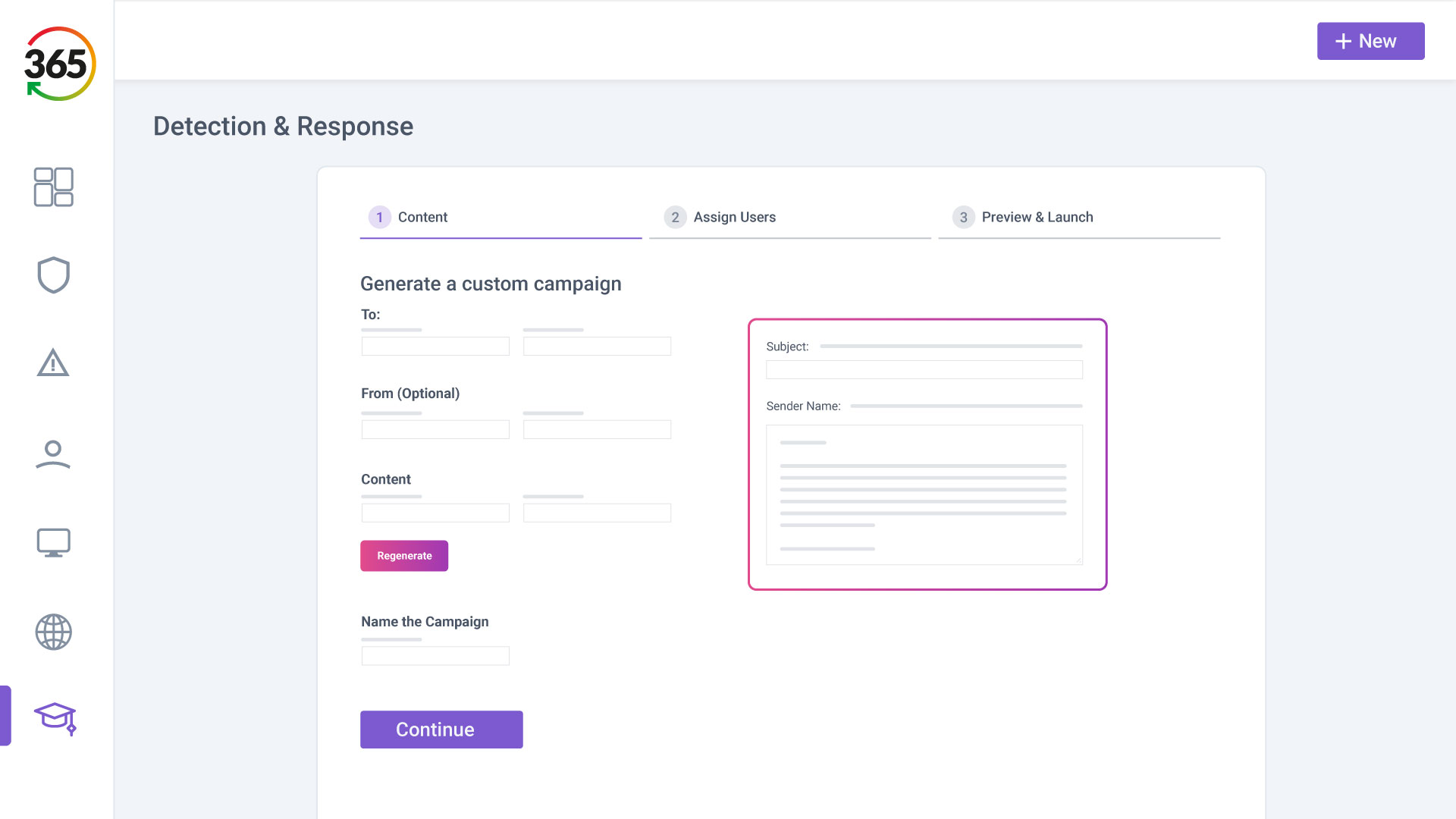
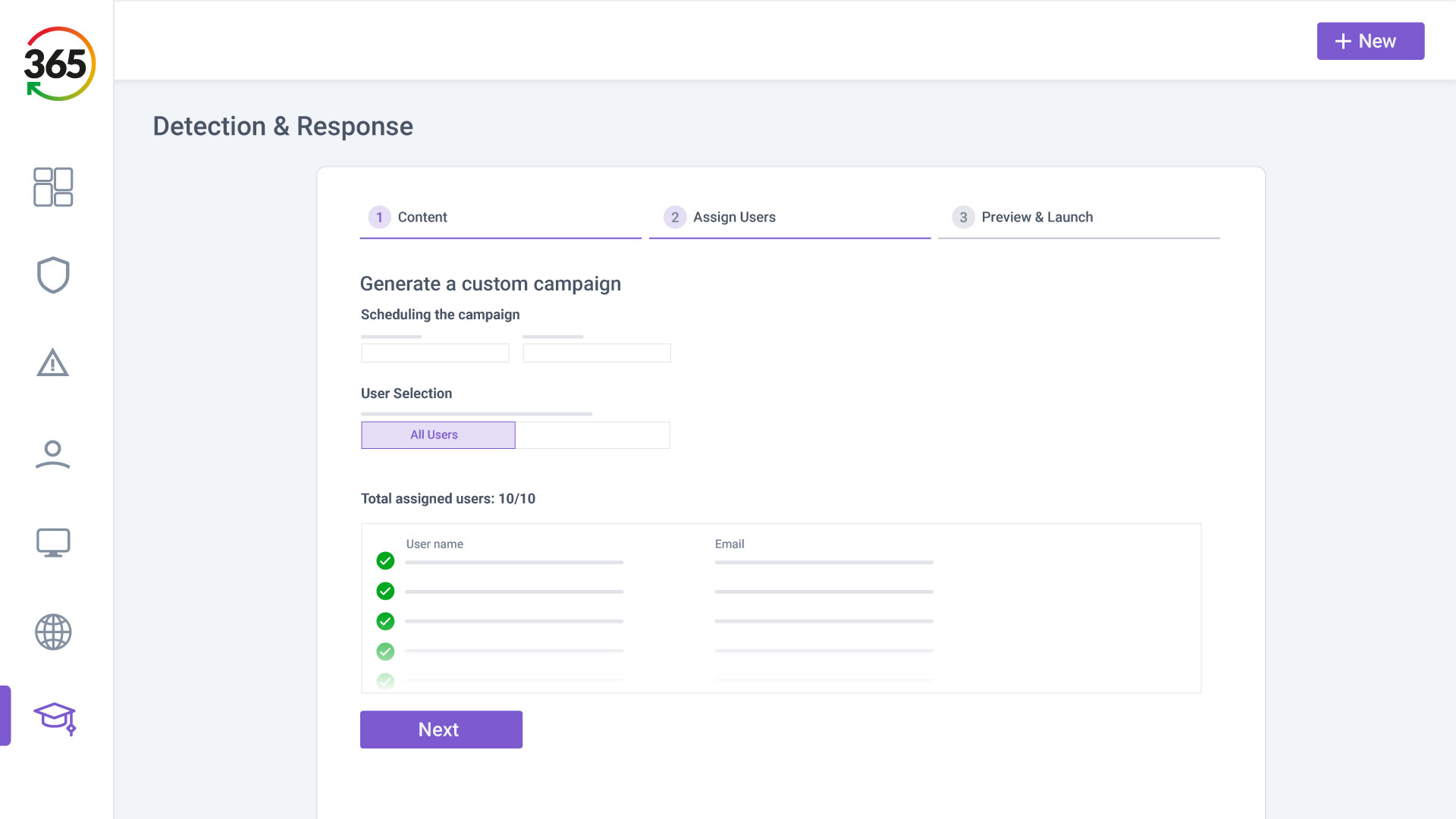
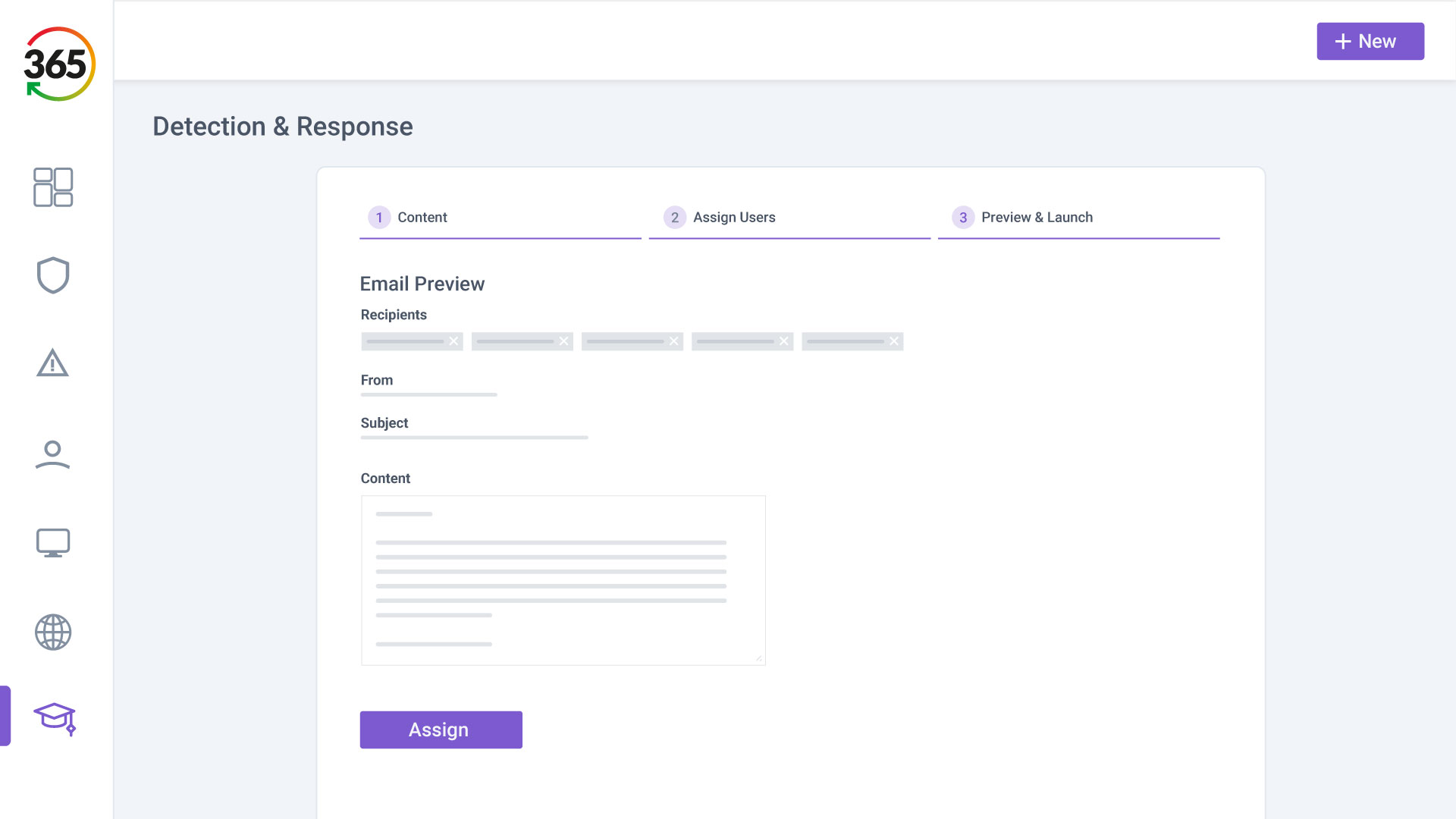
Trust365 is built to fully secure and insure SMEs against ever-evolving threats such as phishing, ransomware attacks, data loss, and user risks by leveraging AI and a multilayered approach.
Follow 4 steps to resilience:
1. FIND
2. FIX
3. SECURE
4. INSURE